Optical Isolation: Your Best Investment for Reliability
In 1999 the Science department at NASA conducted a study on lightning, ground voltage, and structural impact. A building in North Carolina, located within 45 meters of a 42-meter water tower was used in the study. Within a 5-month period, five separate lightning discharges occurred in the area.
While the building itself was never directly struck, it did absorb a high degree of the ground voltage that was discharged from the near-by strikes. The result was “deaths of two trees, a fire in electrical equipment, complete destruction of all phone wiring, and severe damage to electrical fixtures.” (NASA, Science Dept, “Human Voltage”, June 18, 1999)
Unfortunately, this kind of damage to unprotected equipment is not uncommon. The National Lightning Safety Institute estimates that damages of this nature, cost companies and individuals around $4 billion to $5 billion annually. Further punctuating the risk of surge damage, the U.S. National Lightning Detection Network estimates an average of 25 million cloud-to-ground strikes each year.
While the cost in dollars may be alarming, you cannot put a dollar value on human life. The reliability of medical equipment is an absolute must. That is why many of the top manufacturers of medical equipment turn to B&B Electronics for their data connectivity requirements. Our standard off the shelf and custom designed isolation solutions protect your data and valuable equipment in the harshest of environments.
Of course, lightning strikes are not the only originators of high voltage surges that can cause system damage. Transmission line surges, wiring errors, ground loops, and internal complications can also cause transient voltage to run unwanted across networks, phone lines, serial communication systems, and other valuable equipment.
Ground Voltage: An Ever Changing Wave of Potential Destruction
A brief review of what causes the phenomenon of high ground voltage will be helpful in understanding how industrial locations can effectively protect themselves against costly electrical component and equipment damage.
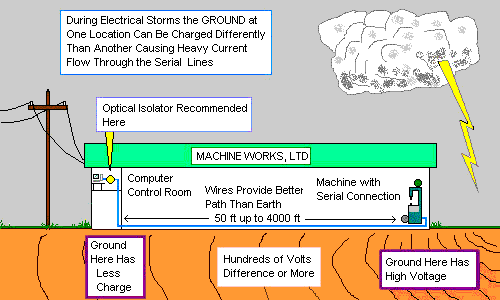
When a high surge of current is released into the ground by a lightning strike (or even something similar like a downed power line), the energy spreads out like a wave. Imagine a large rock being dropped into a still pond. The ripples are more frequent and intense at the point of origin, growing longer and less intense as the wave moves outward.
Similarly, the ground potential at the release point can be hundreds of volts higher that it will be even a few hundred feet away. This difference in voltage levels is the cause of the trouble. As the current moves through the ground, it naturally wants to find a way to equalize and to travel along the path of least resistance. An industrial building found along this path will be connected to the ground, have buried grounding wires, cables and other access points where the current can enter the structure. These wires provide an exponentially easier path for the high voltage to travel across and attempt to equalize.
The result can be large amounts of current entering the building at multiple entry points. It should go without saying that the larger the structure, the higher the potential of transient voltage entering. The damage occurs when this high voltage hits equipment and components that are not capable of handling the sudden surge – the effect is over $4 billion annually in the United States alone.
Minimizing the Risks: An Overview of Protection Systems
Considering the costs of replacing damaged equipment and the impact that downtime has on production and revenue, minimizing the risk of becoming victim to a power surge is essential to every industrial environment.
Here are a few of the surge protection options that you have:
- Surge Suppressors
- Mechanical Isolation
- Optical Isolation
- Triple Isolation
It is important to note that transient voltage, surges and ground loops primarily have two paths they can follow: data lines and ports and power supply lines. Both of these routes provide a “path of least resistance” for surges and must be protected. As is described below, different surge protection components are more suited to protect these different paths.
Here is a summary of the four main protection components available:
Surge Suppressors
Suppression equipment comes in many different shapes, sizes and ratings, ranging from the simple power strip standing between your computer and your power source, to large capacity DIN rail mounted modules. B+B SmartWorx offers several heavy duty, 3 stage surge suppressors. The HESP4DR, 485HESP, 422HESP, and 232HESP are our most popular and robust models. We even offer an Ethernet and USB surge protection with the EIRSP1 model.
A suppressor does just that – it suppresses a surge and dissipates it before it reaches and destroys critical components. Imagine a large dam taking the brunt of a large wave and slowly letting it out through the spill way and you have a fairly accurate concept of how the suppressor operates.
When used properly, or in conjunction with other protection measures, suppressors can be very effective. Suppressors are available to protect power lines and data lines, but are most effective when utilized as a first line of defense on power supply lines. Current models can be DIN rail mounted or connected directly to a cabinet, with surge protection ratings of up to 39kA and less than 1ns response time.
However, several disadvantages and risks must be accounted for in solely relying on suppressors:
- Improper installation
- Poor selection of suppression equipment
- Suppressors typically only protect power lines – not data lines or ports
- And, most notably, what if the “wave” is higher than the “dam”?
This last concern – especially when dealing with large or rapid-succession lightning strikes – has been the demise of many “well protected” systems.
Because of this, in some cases, simply installing a couple of surge suppressors can do more damage than good.
In all cases, those that need a robust solution to protect their data systems and mission critical equipment will need an added layer of surge protection on top of whatever suppressors may or may not be incorporated. Isolation – in varying degrees, depending on the method of isolation used – delivers this added safety net, providing maximum protection from transient voltage.
Mechanical Isolation (Transformers)
Historically, transformers have played a significant role in isolating sensitive equipment. Unlike suppressors that stop surges of high voltage, transformers actually block the DC component of the surge.
Transformers continue to work effectively in isolating systems that utilize modulated signals, such as phone systems and Ethernet communications because of their tightly defined frequency ranges. Additionally, transformer isolation is essential in virtually all AC power transmissions, stepping the voltage down to an appropriate level.
Still, the challenges with utilizing transformers in isolating data circuitry are numerous:
- Transformers are only effective within a narrow frequency range of their design
- High frequency “noise” is transmitted through the transformer and can corrupt data
- Excessive heat builds up when handling high surge levels that can damage equipment
- And transformers – even small ones – have a large footprint, consuming valuable space in frequently crowded industrial environments.
Transformers present another challenge in isolating systems using digital signals, such as those found in serial communication systems. Unmodulated digital data operates at an extremely wide range of frequencies, fundamentally making it incompatible with transformer isolation.
Optical Isolation
The concept behind optical isolation is a simple one and solves the vast majority of data transmission isolation problems presented by transformers and surge suppressors.
Data is brought into an isolation module and converted into a light signal using a tiny light emitting diode (LED). This signal is picked up by a photo diode receptor within the same isolation module and converted back into its original form. The physical gap between the light transmitter and receptor provide the needed isolation from transient current.
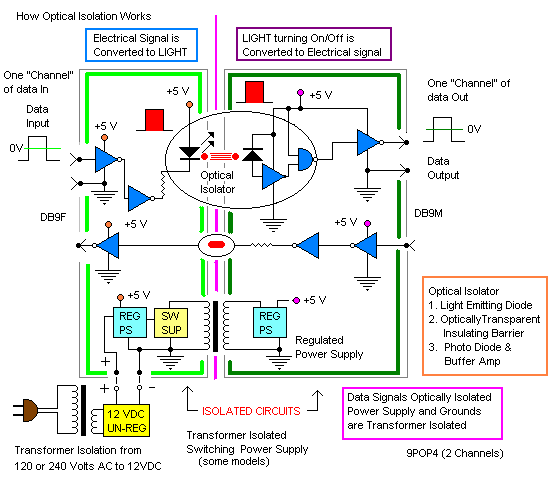
Depending on the need, optical isolation circuitry can be configured in a wide variety of ways. Here are two illustrations of how optical isolation works:
How Optical Isolation Works (with Switching Power Supply)
How Optical Isolation Works (USB)
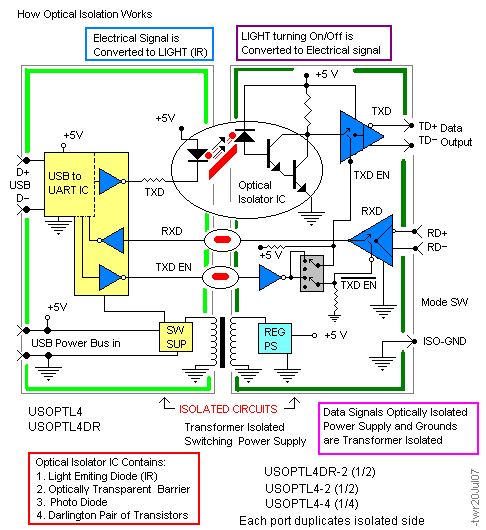
B+B SmartWorx offers optical isolators for virtually any serial protocol. Serial Isolators include DIN Rail models 232OPDR and 485OPDR and a range of in-line isolators.
Triple Isolation
Triple isolation simply extends isolation to each data port as well as the power supply, insuring a completely isolated system. Inside each module, circuitry is strictly separated, with no electrical connections between any two ports of the board. This requires a second, isolated power supply be internally generated in order to power the circuitry of each port of the board.
This kind of isolation represents some of the highest protection you can enjoy in your equipment because it cuts off all available pathways for transient surges and ground loops. Most equipment that employs triple isolation should be able to handle volts in the 2,000 – 3,000 range. B+B SmartWorx models 232OPDRi and 485OPDRi are perfect for situations requiring triple isolation.
Summary
Transient power surges and ground loops can originate from many different sources, including transmission line surges, internal system configuration errors, and, of course, the most powerful source, lightning.
Every year businesses and individuals suffer over $4 billion in damages because they have not taken time to properly protect their valuable equipment. Isolation devices – in their various forms – provide the needed protection.
Are isolation devices more expensive than non-isolated models? Yes. For example, in some cases, an isolated component may cost $30 to $50 more than its non-isolated counterpart.
But what is the real cost? The triple isolation repeater effectively protects equipment located at both ends of the communication line. In most cases there would be a PLC or a PC at one end, with industrial manufacturing or data processing equipment at the other end. With PLC’s running from hundreds to thousands of dollars and other types of equipment running from thousands to hundreds of thousands, the increase in cost to isolate is relatively low.
That being said, perhaps the most important cost to benefit factor to consider when deciding whether or not to isolate, is production time.
How much down time can any given system or piece of equipment sustain before it begins to negatively impact production and revenues? In most industrial situations, down time must be minimized and constantly guarded against, to ensure profitability, good customer service, and acceptable product delivery times.
In the end, by isolating your systems – mechanically, optically, or both – and by establishing “dams” to stop destructive “waves” through the use of surge protectors, you can enjoy maximum up-time and drastically reduce repair and replacement costs due to unwanted power surges.
It is an essential investment that provides maximum protection, while promoting maximum productivity and revenues.
Follow Up Note: Professional Consulting
The maze of what should be protected by isolation and surge protectors and how to properly install the right equipment, can be complex and frustrating. Because of this, B+B SmartWorx offers complimentary professional consulting. Simply grab the phone and call us. Any one of our Application Engineers will be more than happy to discuss your particular situation and provide you with professional grade support and recommendations.
Recommended Posts

Technical Note: Why Network Security is Becoming More Important
August 16, 2018

eBook: Protecting Against Malicious Threats in Ethernet Networks
August 13, 2018

3 Questions to Ask Before Selecting an LTE WAN
June 15, 2018
